What’s the Purpose of Two-Factor Authentication?
Two-Factor Authentication (2FA) works as an extra layer of security online. It’s used to make sure that people trying to gain access to an online account are who they say they are.
How Two-Factor Authentication Works
First, a user logging into an account will enter their username and password. Then, instead of immediately gaining access to the account, the user will be required to provide an additional piece of information. This second factor could come from one of the following categories:
Something you know: A personal identification number (PIN), a password, answers to “secret questions,” or a specific keystroke pattern.
Something you have: A credit card, a smartphone, or a small hardware token.
Something you are: A biometric pattern of a fingerprint, an iris scan, or a voiceprint.

How To Use Two-Factor Authentication
To enable 2FA, you first need to check if the website you’re using supports Two-Factor Authentication. If you are unsure, twofactorauth.org will tell you.
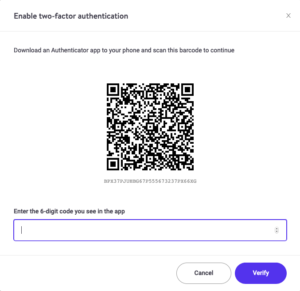
One of the most common forms of 2FA is Time-based One-time Passwords (TOTP). In this case, once you have 2FA enabled within the site or application, you’ll be greeted with a QR code, which you can then scan with an authenticator app (such as Authy or Google Authenticator). Alternatively, an alphanumeric key can also be visible on the screen, which you can manually enter instead of scanning the QR code.
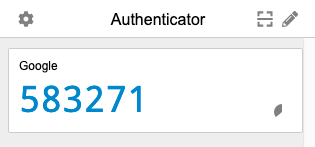
Depending on which authenticator app you are using to manage your Time-based One-time Passwords, a six or seven-digit code will be generated for you that lasts anywhere from 30 to 60 seconds. The shorter the validity period, the higher the security level provided.
As an alternative to setting up an application that manages Time-based One-time Passwords for you, many companies choose to send their users a One-time Password (OTP) via email or text notification. This acts as the second factor required for login and only lasts for a certain period of time or for the current login session before expiring.
After entering the second factor, whether it’s coming from your authenticator app or in the form of a one-time password, you’ll gain full access to the account.
Why Use Two-Factor Authentication?
One of the primary reasons is that widespread major data breaches, which have put hundreds of millions of email address/password pairs up for sale on the dark web, have made many passwords less secure.
According to Verizon’s 2017 Data Breach Investigations Report (PDF), 81% of hacking-related breaches leveraged stolen and/or weak passwords.
Most people reuse passwords across multiple sites and accounts; a hacker can plug in known email address/password pairs into dozens of sites and see which of them provides access.
Using 2FA greatly reduces your risk of having your account hacked because it requires the hacker to have additional information besides the username and password.

Two-Factor Authentication News
Ring, a video doorbell system owned by Amazon, recently made 2FA mandatory amongst its users. Users will need to enter a password and unique six-digit code when they first log in to view their security footage. 2FA had been an option for Ring users before but was not mandatory.
Spotify, a multi-billion dollar music streaming service, still does not offer 2FA to its users. The community has been asking for this feature since 2015, and the company responded a year and a half ago by saying the idea is “Under Consideration.” There’s no clear answer as to if or when it will be implemented.
Conclusion
Privacy is becoming more and more of an issue as technology grows. Whether you are a user or business owner, there are advantages to implementing 2FA. By adding another layer of security to your online account, you are further protecting yourself and reducing the chance of hackers stealing your personal information.